Introduction
Cyber threats are growing every day, and protecting your website from malicious traffic is critical. Among the most popular and lightweight security solutions for web servers are the 7G and 8G Firewalls. These firewalls act as a strong defense layer, blocking malicious requests before they reach your application.
In this article, we’ll explain what 7G and 8G are, why they’re important, how they work (for both technical and non-technical readers), common issues with WordPress, and how TechNetCloud makes managing them effortless — including bypassing false positives.
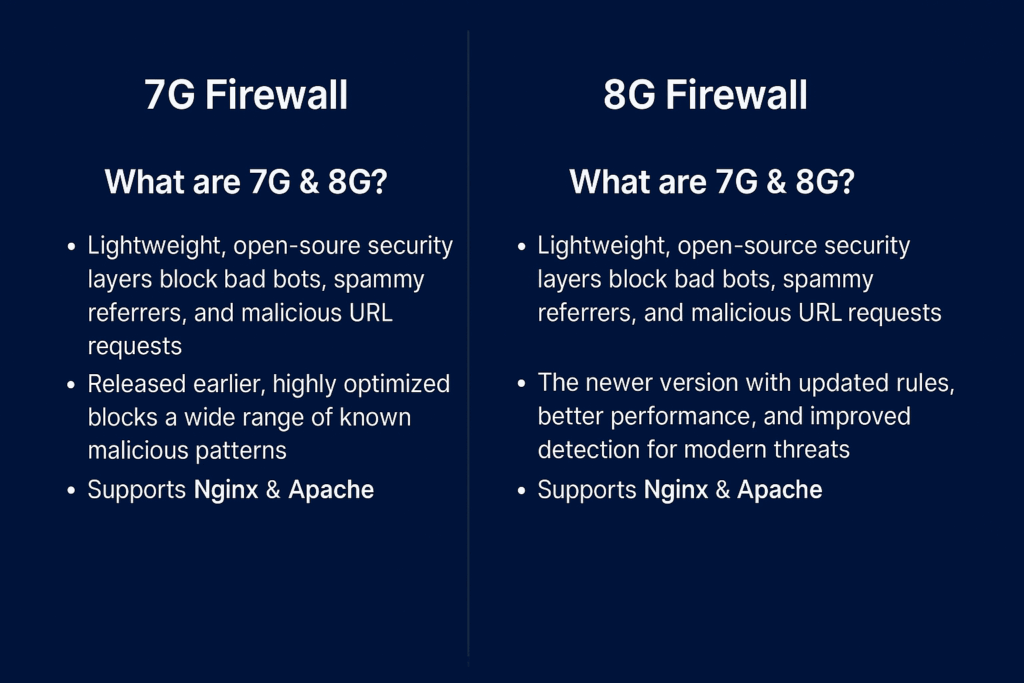
What Are 7G & 8G?
The 7G and 8G Firewalls are sets of Nginx or Apache rewrite rules developed by Perishable Press. They are lightweight, open-source security layers that block bad bots, spammy referrers, and malicious URL requests before they hit your WordPress or web application.
- 7G Firewall – Released earlier, highly optimized, blocks a wide range of known malicious patterns.
- 8G Firewall – The newer version with updated rules, better performance, and improved detection for modern threats.
Why Do We Need 7G & 8G?
- Blocks bad traffic instantly – Reduces server load by stopping requests before they reach PHP/WordPress.
- Lightweight – No heavy plugins; just simple Nginx/Apache rules.
- Proven patterns – Maintained by security experts, continuously updated.
- Easy to implement – Can be applied at the web server level.
Think of them like airport security:
- 7G Firewall = Metal detector + baggage scanner.
- 8G Firewall = Metal detector + baggage scanner + advanced X-ray + AI threat detection.
How Does It Work?
For Technical Readers
7G and 8G work by defining a series of rewrite rules and conditions in your web server configuration (Nginx/OpenLiteSpeed/Apache). These rules inspect incoming requests:
- If a request matches a known malicious pattern (SQL injection, XSS attempt, bad bot), it is blocked with a 403 Forbidden response.
- Otherwise, it is allowed through.
Example Nginx check:
if ($request_uri ~* "(eval\(|base64_decode\()") {
return 403;
}For Non-Technical Readers
Imagine your website as a nightclub:
- Guests (visitors) line up at the door (web server).
- The 7G/8G bouncer checks their ID (request details).
- If they’re on the “blacklist” (malicious pattern), they’re denied entry.
- If they’re safe, they’re allowed inside.
Supported Servers
Nginx ✅
OpenLiteSpeed (OLS) ✅
Apache ✅ (Not the focus here but supported)
Common WordPress Issues with 7G & 8G
Sometimes, legitimate requests may also get blocked. This is called a false positive.
Example:
- You upload an image with a filename that matches a blocked pattern.
- A plugin sends a URL that looks suspicious to the firewall.
These may cause errors like:
- Images not loading
- Certain pages returning 403 Forbidden
- AJAX calls failing
How to Fix False Positives in TechNetCloud
If you’re using TechNetCloud with Nginx, you can easily bypass false positives without disabling the entire firewall.
Step-by-Step:
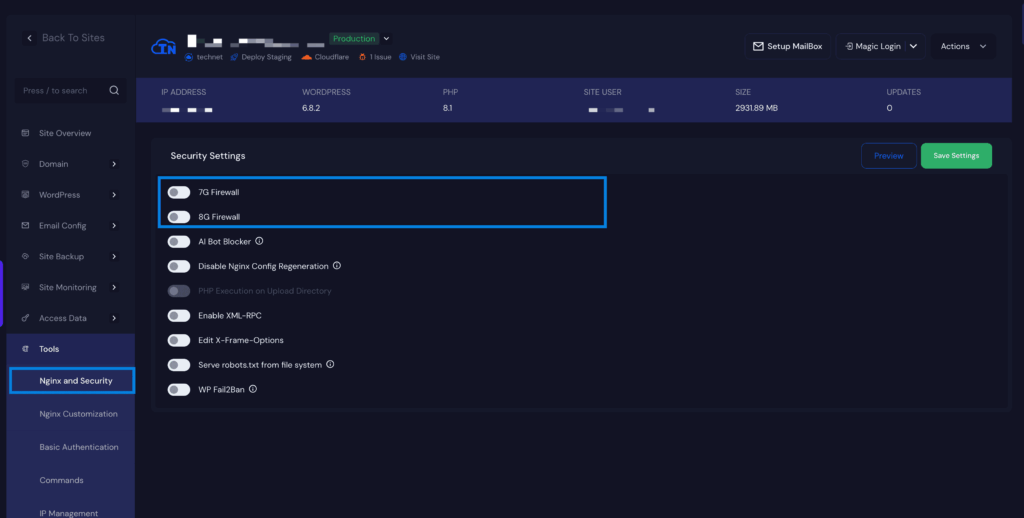
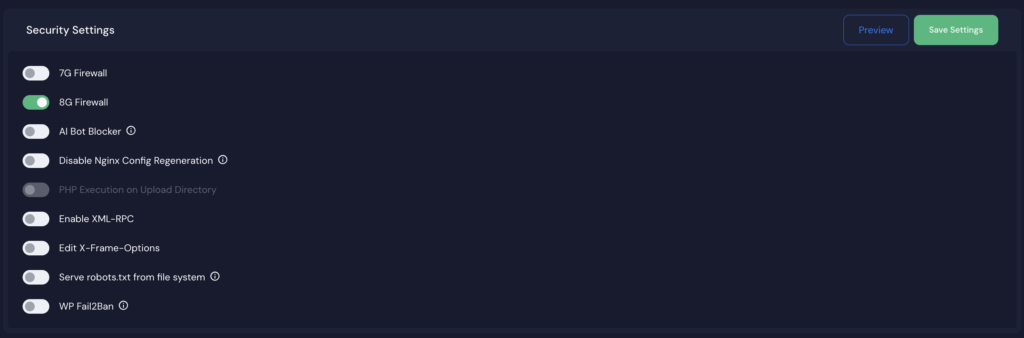
- Enable 7G/8G Firewall
- Go to Site → Tools → Nginx & Security
- Toggle 7G/8G Firewall ON
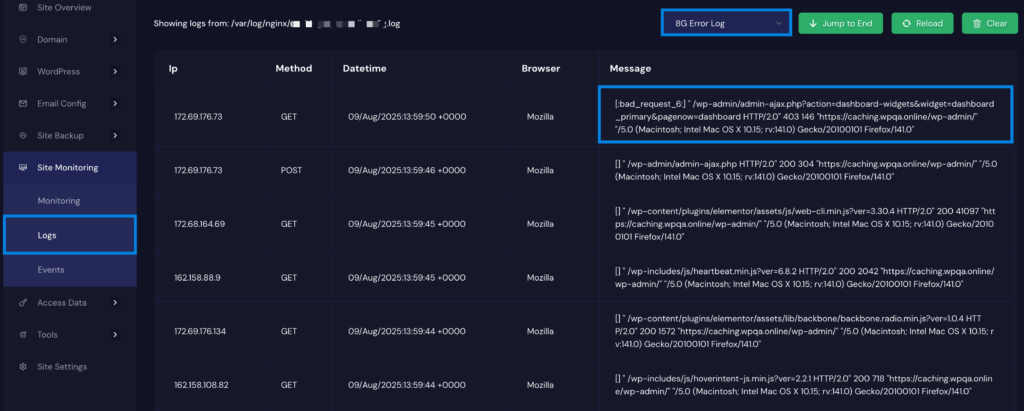
- Check Logs if something gets Blocked
- Path: /server/{serverID}/site/{siteID}/logs and choose 8G Logs
- Or in dashboard: Site Monitoring -> Logs -> 8G Logs
- Look for entries like: bad_request_6
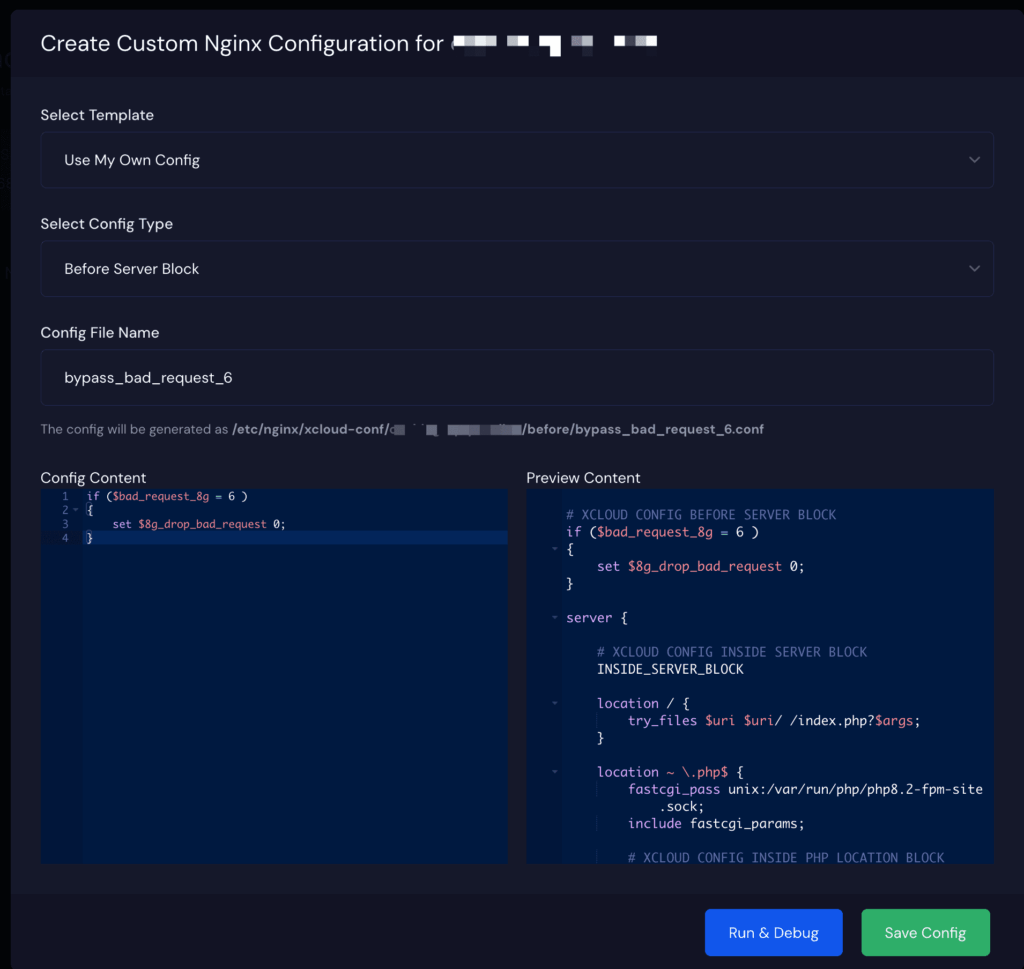
- Bypass the Specific Rule
- Go to Tools → Nginx Customization
- Add a config to bypass bad_request_6:
- Save
if ( $bad_request_8g = 6 ) {
set $8g_drop_bad_request 0;
}
How TechNetCloud Makes It Easy
- One-click enable/disable 7G & 8G without touching code.
- Live logs to see exactly what’s blocked.
- Custom bypass rules for legitimate traffic without compromising overall security.
- Works for all Nginx-based servers — including high-traffic WordPress.
Conclusion
he 7G and 8G Firewalls are powerful, lightweight, and effective solutions for protecting your website from a wide range of threats. While they can sometimes cause false positives, TechNetCloud makes managing them easy — allowing you to stay secure without losing legitimate traffic.
If you’re hosting with TechNetCloud, you’re only a few clicks away from world-class server-level security